|
IDENTIFICATION REPORT
The Identification Report with the trace analysis results
is provided in your web browser window. The report is
separated into the sections described below, and may
vary depending on the information available for the entity
(or ‘target’)
you have traced.
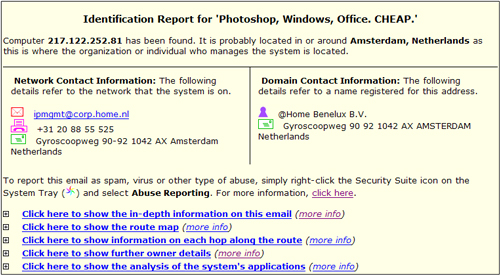
Identification and Registration Summary
The top section of the report summarizes the primary
trace results: the IP address and estimated location,
registration information for the target's domain (if
any), and the network provider, or ISP, providing Internet
service for the target.
Estimated location: The geographical location is a key
piece of information for identifying fraudsters, hackers
and the like. If an email message, website or IP address
is located in a country or region different from
what you expect, and/or from a country known for high fraud rates,
the intentions of the target could well be sinister.
The trace results check the known locations of servers near the target,
and reports the known location when available. If not
available, the location of the target's ISP is provided,
which is usually in the same country as the target, but
may not be in the same city.
Network Contact Information: The network owner, or ISP,
providing Internet access for an IP address or web site, is the company
responsible for reviewing and taking action on abuse reports. In addition,
ISPs are normally located in the same area or region as their users, so the
location of the network provider is often a good estimation of the end-user
location.
Domain Contact Information: A domain is the name
registered by a company, organization or individual that
is used for web site or email adresses, such as ‘visualware.com’.
The domain registration provides details about who has registered a web
site address, helpful information for verifying a web site owner.
Additional identification details are provided
when available, including the time zone, the type of Internet applications
running on the target system, and copyright information from the target
system web page.
In-depth information about an email
This section is reported when tracing an email message you have received (details),
and includes helpful information for identifying the sender of an email message, and/or
evaluating the validity of an email message.
The in-depth details include the IP address of the
computer where the email message orignate, the email
address and other pieces of information that may be
helpful in identifying the sender or the sender's intent.
For example, a common trick deployed by the originators of email
abuse (such as spam, phishing and virus emails) is to insert false
headers into the email in an attempt to hide the source of the
message. The real headers and false headers get muddled together,
creating a sort of ‘digital smoke screen’ so
it is difficult to know which header is the originating
header. This process of trying to hide the originator
is an illegal act called misdirection. eMailTrackerPro
sees through this technique, identifies which headers
are real and false, and reports the act of misdirection.
You can be sure that any email with misdirection should
not be trusted.
The in-depth details also reports the computer name when available, which is another
important clue to the target's identity as it is common for computer owners to use
their own name or online alias for their computer name.
Route Map
The map section of the report shows the Internet route between your
location and the target being traced.
A solid line represents a known location in the
Visualware database, and a dotted line represents an estimated
location which is derived from the registration details
for the target's ISP. The Internet route is an important
piece of evidence when tracking a target's location
as it represents a trail to the destination. While
the estimated location is usually correct at a country
level, any city locations identified as 'known' that
are close to the target destination further help to
qualify the target's physical location at the city
level.
Route Table
The route table shows each segment, or network ‘hop’ of the
the Internet route between your location and the target being traced. While
both the Route Map and Route Table show the Internet route, the Route Table
provides more detail that can be examined for clues to the target's location.
Locations in bold are known locations
that have been identified by the Visualware IP location
database. Locations in parentheses are estimated locations
that are derived from registration databases. While
estimated locations are usually correct at the country
level, any known locations that appear in the last
2 or 3 rows are a good indicator of the target's physical
city location. For example, in the route table above
the target is likely to be located in the Burbank,
CA, USA or nearby surrounding area.
Further Network Details
This sections provides the complete registration information for the
target's ISP and domain (when available).
While the Network and Domain
Owner details are summarized in the top summary section
of the Identification Report, the complete registration
records are provided in this section as they often
contain additional contact information that may be helpful
in tracking and reporting a target.
Analysis of the System's Applications
This section provides a report detailing any Internet services that may be
running on the target computer being traced.
The type of applications running on a target system is useful
information as it can provide insight into the ownership
and geographical location of the target. The most common
applications on the Internet are web servers (websites,
HTTP), mail servers (email, SMTP) and file transfer
servers (file downloads, FTP). As an example, web server
applications (such as www.visualware.com) are particularly
useful because web pages along the lines of ‘contact
us’ often
exist to provide details such as names, phone numbers
and other contact related information.
|